How to get online part 3: Securing your website
On the third instalment of ‘How to get online’, we wanted to cover something super important – securing your website. You need to make
How to get online part 2: Building a website
The second step in our five-part series; ‘How to get online’ is to build a website. Once you’ve accomplished step one (registering a domain),
How to get online part 1: Registering a domain
This is the first instalment of our new five-part series; ‘How to get online’. We’ll go through all the steps you need in order
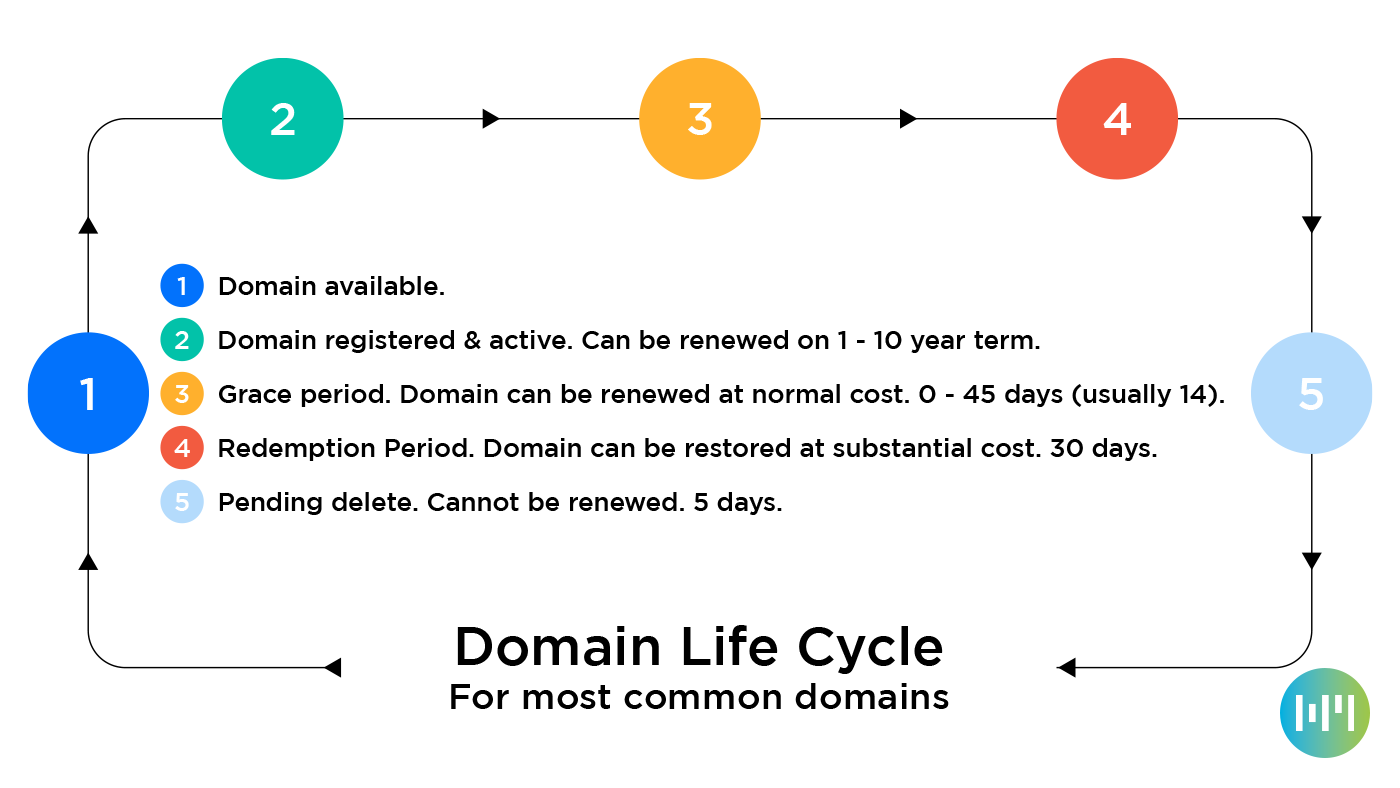
The lifecycle of common domain name extensions
.com, .net, .org etc domains The following image depicts the lifetime of a .com .net or .org domain Once a domain enters the ‘Redemption Period’
Choosing the best hosting company for my website
In this article we will cover some of the important aspects of choosing a hosting partner for your website hosting, email hosting or domain
5 Reasons you need an SSL certificate
What is an SSL certificate? SSL stands for Secure Sockets Layer and is the standard technology for establishing an encrypted link between your browser
My site contains malware, what does that mean?
This essentially means that your websites security has been compromised and malicious files uploaded to your sites folders. Once those files have been uploaded,